
Table of Contents
Case 1
Executive summary
Digital crime has become quite frequent in various multinational companies and IT firms. In this case, study, an employee of a reputed IT company has been accused of digital illegal activity and has presented the memory image of the employee’s system’s hard disk. In this report, the paper has presented the proper sequential order of investigation. The report therefore presents the authorisation and preparation of the collected documents, measures undertaken for handling the evidence, an overview of the examination procedures and results. The report has also presented the reconstruction report of the entire investigation as well. [Refer to the appendix]
Authorization and preparation
In case of digital forensics, the authorisation of the gathered evidence refers to the analysis of the electronic evidence and media for acquiring confirmation. This authorisation or authentication of the electronic evidence includes confirmation regarding evidence such as the origin of the evidence, tracking the time strap of the evidence and composition along with composer ID (Davies & Smith, 2019). In this case, study, a memory image has been taken as evidence from the hard disk of the employee’s computer. Therefore, based on this memory image and proper application of Memory Forensics, it will be possible to track various crucial aspects, such as, running procedure, executable running files on that system, information regarding the IP addresses and other networking sources. The proper authorization of the memory image will also help to analyse the users who have logged into the system previously and the details regarding the usage of various files and folders. Therefore, in this case the memory image has been authenticated based on the Hibernation File and Page File as well.
On the other hand, for the preparation of this evidence, procedures such as staff monitoring, securing data to the evidential standards, ensuring legal sensitivities in respect of the law enforcement as well (Rizal & Hikmatyar, 2019).
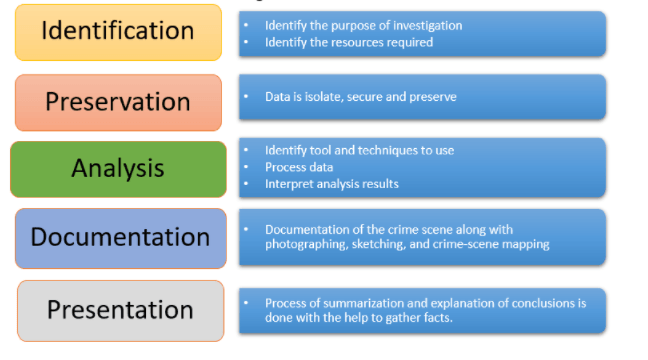
Figure 1: Process of Digital Forensics
(Source: Rizal & Hikmatyar, 2019)
Evidence handling
After gathering authentication and preparing the evidence, it is important to handle the gathered data properly (Ruuhwan et al. 2017). Here in this case, the primary evidence, the memory image in the hard disk of the employee has been subjected through the following procedure-
- The contents of the hard drive have been examined to identify the recent activities within the system and recording the information regarding particular system.
- Digital photographs have also been taken of both the original and the duplicate media as well.
- Both the original and duplicate media along with other potential evidence has been placed with an evidence tag for a better identification.
- Among all these potential media the best and the most crucial evidences have been secured safely to the separate application and system.
- The examinations and tests have been run on the duplicate copy or working copy to ensure no damage is brought to the original ones.
- The tests have been run under the vigilance of a principal invigilator and evidence custodian to ensure impartiality and clarity within the investigation procedure.
- A monthly audit has been presented to ensure the safety and security of the gathered evidence (Du et al. 2017).
Analysis and Examination
Examination Procedure
In case of examining the collected information and evidence it is important to apply a proper tool of digital forensic. Since in this case the forensic evidence is a memory image stored in the hard disk of a computer, therefore, there have been various essential and proper tools for memory forensic (Page et al. 2019). These tools may include Volatility Suite, Rekall, Helix ISO, Belkasoft RAM Capturer or Process Hacker. In this case, Process Hacker Software has been used to analyse the evidence. In order to analyse and examine the gathered information from the tools, at first, the applications within the memory are decoded (Sommer, 2018). With the help of this decoding, it has been able to identify the presence of the malware that has been presented within the encrypted system or encrypted files. The decrypted vision of the memory image has therefore been able to detect the cipher or the hash within the encrypted system and examine the activity more accurately.
Figure 2: Types of Forensic tests
(Source: Sommer, 2018)
In addition, another major step for this examination procedure has included time strap comparison and decoding the network information. With the application of the time strap configuration, it has been able to identify the time strap of the interference of the malware on the host’s system files (Sommer, 2018). This test has made the investigation to gain access over the browser history of the malware author, establishing correlations between date and time of the malware of illegal activities. On the contrary, with the help of decoding the network information, the investigation has been able to prevent further spread of this infection. In addition, identifying the network information has also helped the investigators to detect the source of the IP address that the malware function reverts to. This test has also identified frequency of malware communication with the target system that detects the infected portions of the host’s systems as well.
Analysis
From the examinations that have been conducted in this case, during the decoding of the memory image it has been observed that the decrypted file here has been identified with the presence of a malware that has been reverting to an IP address present within the same system. In addition, with the help of network information analysis, the browse history has revealed a frequent communication of the malware to the some restricted IP address of the company profile along with particular date and time.
Figure 3: Digital Forensic test
(Source: Sommer, 2018)
Reconstruction and reporting
In case of digital forensic, the concept of reconstruction refers to the determination of the incident sequence within the entire malware activities. During the process of reconstruction, the principal investigator observes and arranges the key incidents within the sequential order and presents it to the court (Page et al. 2019).
Here, in this case, the suspected employee has got access to a malware tool that has helped him to decrypt all the confidential information and facts from the organisation and sell to the rival organisation and claiming ransom from the victim company as well. With the help of the malware, he had decrypted relevant information regarding the customer profiles and the business strategies through frequent communication in more than 4 to 5 transactions. In addition, with the help of another malware, he has also tried to blackmail the victim organisation to collect ransomware regarding the customer credentials and sold the important credentials to rival organisations.
Conclusion
Therefore, based on these results achieved from various digital forensic tests and examinations such as, the time strap configuration, the memory decoding and network identification, it has been observed that the memory image of the accused employee’s hard disk has shown the presence of some malware and traces of illegal activities. These activities of getting access to confidential company credentials and access over customer information stand completely against the privacy policy of the company. Therefore, in this case study, the blames that have been conferred upon this employee has hence been proved true.
Case 2
Abstract
Cloud forensic has an extended part of digital forensic that allows a cross-sectional investigation and allows recovery of deleted data and information. In this assignment, the paper has therefore presented a critical evaluation of the forensic tools and techniques. The paper has also presented processes, challenges and recovery solutions for Cloud Forensics.
Introduction
In today’s digital world, digital crimes and illegal activities have become quite frequent. In the case of cloud computing as well, digital crimes have significantly increased. Therefore, Cloud Forensic allows the user to ensure the safety of the encrypted files and maintain the confidentiality of the same. In other words, this can be said that Cloud forensics is basically the extended application of digital forensics that specialises in cloud computing and helps to collect and preserve the essential evidence to present before the law. In this case study, the IT manager of a reputed company has become concerned regarding the safety aspect of day-to-day transactions and digital monitoring of the company. Therefore, it is important to imply various useful tools and measures to ensure safety and proper maintenance of the digital activities.
Technical Background
Cloud computing tools and technologies have shown massive progress in providing safety and security in the case of cloud computing. Cloud forensic has become more significant in terms of the radical features of altering information (Janarthanan et al. 2021). In case of IT industry, the basic infrastructure of the company becomes solely dependent on cloud technology therefore, it becomes important to maintain the security of the users from unknown threats, such as, malware and ransomware. Therefore, in case of cloud forensics, there have been various tools and technologies for identification of any intrusion or falsification within the system. In this case study since the organisation deals with their day-to-day activities and transactions on the cloud based platform, therefore, it becomes important to take measures of these following tools.
Frozen
Among all the tools available within the market, FROZEN appears to be one of the most efficient and effective tools. FROST has been one popular forensic tool especially designed for OpenStack Cloud Computing. With the application of this particular tool the user becomes able to store the log data in the Hash trees and revert it back in its cryptographic forms as well (Moussa et al. 2019). In addition, since the tool works on the user plane therefore, it possesses the minimal requirement for interacting with the operating system of the virtual machine of the guest. In addition, with the application of FROST, the IT manager in this case will also be able to draw the required information from the OpenStack Cloud system, without interacting with the provider’s systems.
UFED Cloud Analyser
Another major tool for ensuring the safety and recovering data from cloud computing involves UFED Cloud analyzer. With the application of this cloud forensic tool, the investigator becomes able to derive a large amount of essential data and information while investigating. The cloud sources here act as the mine of valuable and sensitive data (Uphoff et al. 2018). This particular tool helps to extract log-in credentials to get access to the previous user. In addition, this application also helps to preserve the forensic data and allow the investigators to get a unified format for their visualisation. On the other hand, with the application of the forensic tools, the investigators can also report, export and share the extracted data.
Other than these two specific tools, the two effective techniques can also be followed, for instance, Speeding cloud data and extracting them remotely (Akter, 2020). With the application of this particular tool, the investigator becomes able to track and break the malware’s previous activity logs, extract details regarding the location of the malware users and track their location history as well. In addition, with the help of this technology, the user can also get a progressive view including the thumbnails, timeline, maps, contacts and files as well.
Network Forensics/Cloud forensics: process, challenges and solutions
Network Forensics or Cloud Computing includes the procedure of identifying the malware, collecting the evidence preserving the evidence in a secured away, running test examinations, conducting analysis and reporting the digital evidence as well. In the case of cloud computing, the major challenge that arises for the users lies in the fact that the customers do not get any access to their log files (Bhagariya et al. 2021). In case of an investigation, the cloud service providers generally do not provide any sort of segregation regarding their responsibilities towards their customers. Therefore, it becomes quite difficult for the user to recover the data in case it is lost or gets deleted (Alenezi et al. 2017). Since, in case of cloud computing, the data of the user’s system may reside at different geographic locations in various machines, therefore, recovering the deleted data or stolen information becomes quite challenging for the investigator or the user as well (Neware & Khan, 2018). Therefore, the concept of cloud forensics has become essential in today’s scenario. The other challenges of Cloud Forensic includes getting transparency and clear outlook to the API of the Cloud Service provider as well. However, in order to solve these issues, it is important to incorporate an Account Based Approach (Manral et al. 2019).
Conclusion and Future works
Therefore, to conclude with, this can be said that the importance of Cloud forensics become evident whenever, there arises any sort of unauthorised or suspicious access to the confidential data and information. In this case study, in order to monitor the daily activities and monetary transactions, the IT manager can therefore include these forensic tools and technologies in future to ensure the protection of the confidential and sensitive data as well.
Reference List
Akter, O., Akther, A., Uddin, M. A., & Islam, M. M. (2020). Cloud Forensics: Challenges and Blockchain Based Solutions. International Journal of Modern Education and Computer Science, 10(8), 1-12.
Alenezi, A., Hussein, R. K., Walters, R. J., & Wills, G. B. (2017, April). A framework for cloud forensic readiness in organizations. In 2017 5th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud) (pp. 199-204). IEEE.
Bhagariya, K., Sheth, R., & Dholariya, M. D. (2021). Cyber Crime Investigation and Preventing in Reference for Cloud Forensics: A Review.
Choo, K. K. R., Esposito, C., & Castiglione, A. (2017). Evidence and forensics in the cloud: challenges and future research directions. IEEE Cloud Computing, 4(3), 14-19.
Davies, G., & Smith, K. (2019). The Feasibility of Creating a Universal Digital Forensics Framework. Forensic, Legal & Investigative Sciences, 5(1), 1-9.
Du, X., Le-Khac, N. A., & Scanlon, M. (2017). Evaluation of digital forensic process models with respect to digital forensics as a service. arXiv preprint arXiv:1708.01730.
Janarthanan, T., Bagheri, M., & Zargari, S. (2021). IoT forensics: an overview of the current issues and challenges. Digital Forensic Investigation of Internet of Things (IoT) Devices, 223-254.
Manral, B., Somani, G., Choo, K. K. R., Conti, M., & Gaur, M. S. (2019). A systematic survey on cloud forensics challenges, solutions, and future directions. ACM Computing Surveys (CSUR), 52(6), 1-38.
Moussa, A. N., Ithnin, N., Almolhis, N., & Zainal, A. (2019, August). A Consumer-Oriented Cloud Forensic Process Model. In 2019 IEEE 10th Control and System Graduate Research Colloquium (ICSGRC) (pp. 219-224). IEEE.
Neware, R., & Khan, A. (2018, March). Cloud computing digital forensic challenges. In 2018 Second International Conference on Electronics, Communication and Aerospace Technology (ICECA) (pp. 1090-1092). IEEE.
Page, H., Horsman, G., Sarna, A., & Foster, J. (2019). A review of quality procedures in the UK forensic sciences: What can the field of digital forensics learn?. Science & justice, 59(1), 83-92.
Rizal, R., & Hikmatyar, M. (2019, July). Investigation Internet of Things (IoT) Device using Integrated Digital Forensics Investigation Framework (IDFIF). In Journal of Physics: Conference Series (Vol. 1179, No. 1, p. 012140). IOP Publishing.
Ruuhwan, R., Riadi, I., & Prayudi, Y. (2017). Evaluation of integrated digital forensics investigation framework for the investigation of smartphones using soft system methodology. International Journal of Electrical and Computer Engineering, 7(5), 2806.
Sommer, P. (2018). Accrediting digital forensics: what are the choices?
Uphoff, M., Wander, M., Weis, T., & Waltereit, M. (2018, August). SecureCloud: an encrypted, scalable storage for cloud forensics. In 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE) (pp. 1934-1941). IEEE.
Appendix: The Memory Image

(Source: https://ccm.net/faq/578-how-to-increase-the-cache-on-your-hard-disk)
